Ethical hacking is a hot job market right now. With the uptick in companies getting hacked and a rise in personal data being stolen, organizations are in need of individuals that can design and carry out a penetration test in order to gauge their security posture. Organizations like Michael’s, Target, financial institutions, and government agencies have all been targets of hackers both foreign and domestic. There are many certification tracks out there today that help to validate your skills as a penetration tester or ethical hacker such as the Certified Ethical Hacker, PenTest+ and many more.
Having ethical hacking skills is great, but how does one go about building those skills and constantly refining them? One method that has proven to prepare someone for a certification exam and help them continually refine their skills is having a home lab. An ethical hacking home lab gives you the opportunity to test out the latest and greatest ethical hacking tools and hone your penetration testing skills. A question I get frequently is how to build an ethical hacking lab, and specifically how to do it affordably. The answer varies. It depends on what you currently own, and what your budget is. Here is a guide to help you build an ethical hacking lab that will allow you to test your skills and build a good foundation for legal hacking.
Hardware for an ethical hacking lab
In most cases you can use just about any old laptop or PC you might have lying around. You will generally have better luck with a PC with a decent amount of RAM (at a minimum 16 GB, 32 is better). The one important thing to ensure is that your PC’s CPU is virtualization capable. The way to check this is to boot your PC and bring up the BIOS menu, in the BIOS menu you will see a setting under “Advanced” that reads “Intel Virtualization Technology.” That setting has to be enabled, see the image below.
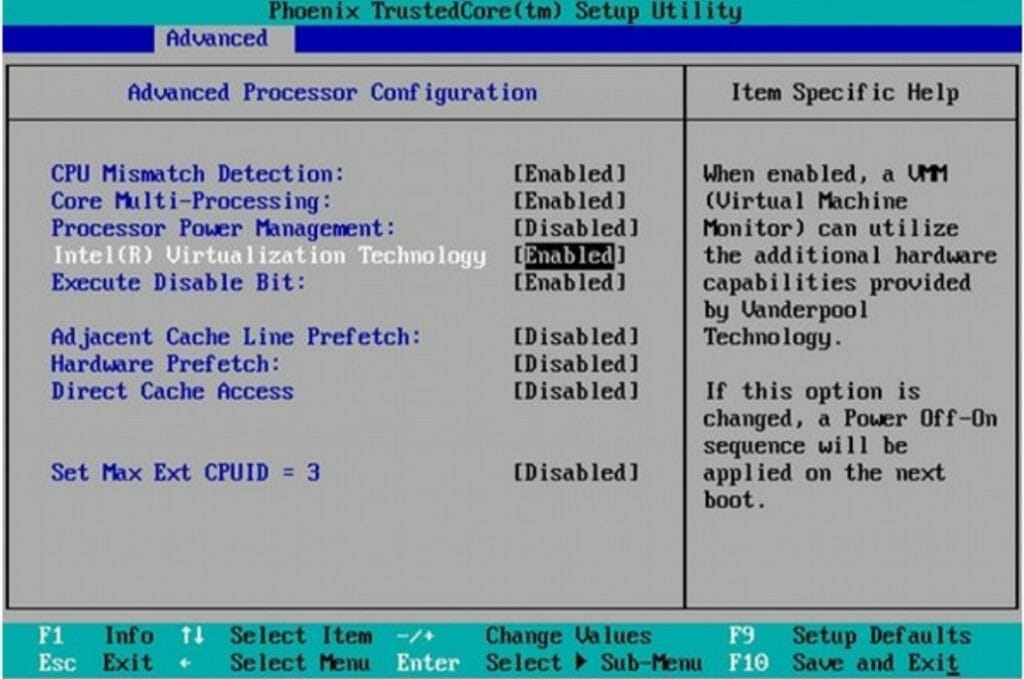
If you have this setting and it is enabled, you are good to go!
Software for an ethical hacking lab
Since having an ethical hacking lab will require you to build several computers, you can do this on the cheap if you utilize software that will let you build virtual machines. In this example I’m going to use VMware as an option. There are other virtualization platforms you can use such as VirtualBox or Parallels, but for the purpose of this article, I’ll be using VMware Workstation. Workstation will set you back $150, but it is worth it, as there are many great features you can use such as snapshots and cloning. With VMware Workstation installed, you can start building virtual machines.
Tools for an ethical hacking lab
As for tools, there are so many ethical hacking/penetration testing tools out there it can be hard to keep track. Thankfully, there is an awesome Linux operating system called Kali Linux. This is hands down the most important part of your ethical hacking lab (see the desktop image below).
Kali Linux is a Linux distribution that comes loaded with just about every ethical hacking tool you could think of. Most importantly, it comes loaded with Metasploit which is a very well known hacking tool set. Other tools that come loaded with Kali are used for information gathering, vulnerability analysis, password attacks, wireless attacks and so much more. The best part of Kali Linux is that it’s free! So many awesome tools, and all free. On top of installing Kali in your VMware Workstation, it is a good idea to install one or two Windows VMs so that you can tamper with them without messing up any of your own personal stuff (if you use Windows). Of course, with Windows, there is a licensing cost, can’t get around that (legally anyways).
Practice Labs
Once you have the tools and you have Kali installed, you then need to do something with it. Where do you start? There are so many practice labs available on the web, here are a few suggestions of where to start.
- Boson Practice Labs for Ethical Hackers – $99
- LearningTree International Ethical Hacking Essentials Labs – $149
- Measure Up: ECCouncil Practice Lab: Ethical Hacker – $149
Do it Legally!
This is not a post meant to encourage individuals to try their hand at hacking just anyone or anything. This post is meant to help you on your way to becoming a Certified Ethical Hacker or penetration tester, in a legal fashion. The one rule for ethical hacking is to always ensure you have 100% implicit permission to hack someone’s systems or just stick to hacking your own systems on your own network. If you try it any other way, you could end up in hot water with law enforcement. Do it legally; we need more good guys out there defending systems and helping organizations become more secure.