In a rare December 2018 public address, British Secret Intelligence Service (SIS) Chief Alex Younger used the term ‘fourth-generation espionage’ to describe the new mindset that intelligence leaders needed to address the challenges of the fourth industrial revolution. He noted that “The digital era has profoundly changed our operating environment. Bulk data combined with modern analytics make the modern world transparent. We need to ensure that technology is on our side, not that of our opponents”.¹
New Technologies = Changing Espionage Tactics
Younger’s concerns are well founded. The Fourth Industrial Revolution includes many new technologies that complicate clandestine activity, including “mobile devices, Internet of things (IoT) platforms, location detection technologies (electronic identification), advanced human-machine interfaces, authentication and fraud detection, smart sensors, big analytics and advanced processes, multilevel customer interaction and customer profiling, augmented reality/wearables, on-demand availability of computer system resources, and data visualization.”²
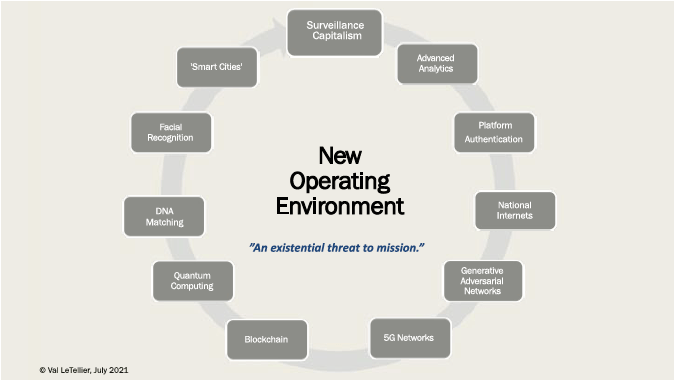
In fact, the combination of ubiquitous digital surveillance and powerful data analytics is changing espionage in ways that we are only starting to understand. What we do know is that widespread automated recognition and monitoring of individuals is now possible, ‘blind spots’ are quickly being eliminated, events can be forensically examined to the degree never known, and an individual’s future actions quickly and accurately predicted.
This comes through expansive closed-circuit television (CCTV) camera placement, ‘smart city’ technologies, ad-tech data, vehicular telemetry, IoT, and 5G networks enabling omnipresent personal data collection and the data analytics to make sense of it all; machine learning that enables massive data aggregation, facial recognition for real-time monitoring and post-event investigation and pattern analysis for identifying anomalies and predicating behavior.
Finally, the artificial intelligence (AI) capabilities, ‘multi-intelligence fusion’ methodologies and correlation engines currently under development will certainly enable counterintelligence by further empowering aggregation and seamlessly integrating different sensor types.
Digital Storm Clouds Building
Law enforcement and counterintelligence elements now have an exponentially growing array of digital sensors and robust analytics to collect and turn massive data pools into usable information, allowing them to increase accountability within their governments, prevent external and internal actors’ activity, and quickly investigate suspect activity.
This ‘perfect storm’ of exploding data collection, powerful data analytics and even virus tracking creates what some have called ‘an existential threat’ to the ability of intelligence agencies to conduct mission. To better understand these challenges and what intelligence agencies need to do to address them, it is helpful to examine the impact of the new operating environment on select human intelligence activities:
First, think about widespread personal data collection and the impossibility of privacy and effective cover. Advanced data analytics, machine learning (ML) and AI enable the aggregation of massive data sets, the correlation of activity and the real time and forensic exposure of operations. High-speed/high-density 5G cell networks, IoT devices and vehicle telemetry provide refined triangulation and location of an individual’s movement, further complicated by emerging issues like DNA mapping and virus tracking.
Second, think about the massive expansion of the virtual domain where many people now spend more time than the physical world. The ability to operate safely, securely, sustainably, and successfully online are ‘table stakes’ for any modern-day service, underpinning a wide spectrum of activity like information collection, targeting, influencing, and recruiting. COVID’s restrictions have only accelerated and reinforced this point. Meanwhile, cyberspace is becoming more active, unforgiving, and hostile. Data providers and social media platforms are monetizing their access through stronger authentication and adversary services are increasingly aware of traditional methodologies. Emerging national Internet networks in Russia and China challenge the ability of intelligence agencies to electronically travel there. Generative adversarial networks (GANs) are enabling advanced deepfakes and impairing the ability to detect false information/personas and tailored social engineering.
Finally, blockchain technologies and cryptocurrency enable non-attributed payments and complicate the ability to “follow the money” and quantum computing can threaten communication security tools and enable the decryption of what was one secure data collected by adversaries.
Now think of these not as single problems you have the luxury of time to address one at a time, but as concurrent challenges simultaneously undermining traditional tradecraft methodologies. The challenge is daunting.
Bottom line, these challenges require a new approach and innovation. The speed of change in this domain is remarkable, meaning that operators constantly need increasingly sophisticated support for an increasing breadth and depth of challenges.
New Operating Environment REquires Intelligence to Evolve
Specifically, different solutions are needed for different missions to identify, quantify, and mitigate digital surveillance risk ranging from growing big data aggregation to street level ‘smart city’ applications. For virtual operations, intelligence agencies need to counter ever-changing and evolving authentication measures by social media platforms, including biometrics and liveliness tests. These changes further test their ability to look real to platforms, targets, and adversaries and achieve scalability, and practice an ‘art form’ that requires a choreographed blend of technology, talent, and tradecraft.
That said, the news isn’t all bad. Some elements of this new tradecraft should come naturally as intelligence agencies leverage ‘technological reciprocity’; offensive solutions enabling defensive solutions and vice versa. For example, by developing refined digital targeting one can inform the development of digital surveillance countermeasures, by developing specialized payment mechanisms one can strengthen one’s understanding of adversary payment tradecraft, by applying new data analytics one can reveal adversarial data methodologies and vulnerabilities, and by red teaming one’s processes one can reveal indicators for adversary activity identification.
Traditional tradecraft is already being publicly proven inadequate for today’s new operating environment, reinforcing that the arrival of the fourth industrial revolution is an inflection point for many intelligence services; separating those that harness advancing technology to their advantage from those that fall victim to it.
American intelligence services must also “evolve or die” to maintain the degree of effectiveness and relevance they’ve had up to the present. First, they must make their workforces aware of the impact of the modern technologies upon their respective missions and then invest the necessary resources to develop ‘next generation tradecraft’ methodologies, capabilities and solutions to counter or harness specific technologies against their operational goals. Given that the technological advancement we’re witnessing is predicted to only accelerate under its own momentum into the coming decades, falling behind on these responses will have long lasting impact to each organization’s capacity to execute mission and the overall strength of the United States Intelligence Community.
1 Alex Younger, 3 December 2018 https://www.gov.uk/government/speeches/mi6-c-speech-on-fourth-generation-espionage.
2 Wikipedia, June 2021