Pokemon Go … unless you’ve been totally disconnected from the electronic world we collectively share, you’ve heard of the Pokemon Go phenomena. Indeed, the national media is carrying a plethora of stories on the virility of this online game played using one’s mobile devices (iOS or Android). Some of these stories have legs, others are simply folks making stuff up as they play the game to draw attention to themselves. There are areas where you need to pay attention and realize what’s going on, as you may, could, and can put yourself or your connected devices at risk of compromise.
Privacy – Pokemon Go accessing your data
According to the ARS Technica, “iOS version of Pokémon Go is a possible privacy trainwreck.”
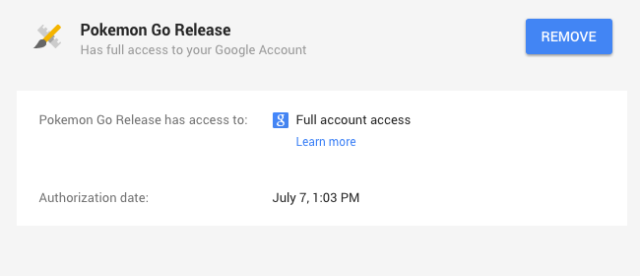
Indeed, as seen in this iOS version of Pokemon Go, the user is giving the application (app) full access to their Google Account. That said, Niantic (the makers of Pokemon Go) advise that they are going to be updating the iOS version of the app soon, and that while the app does have permission to access those portions of the Google services you use, they aren’t using anything more than your name and email address. Separately, Google advised that they are working to reduce Pokemon Go’s access as well. Your call.
What about those using Android devices? The coding is slightly different and the app does not appear to be requesting the same depth of permissions when users sign in with their Google account credentials.
Malware – Pokemon Go downloads with RAT
As millions of users download Pokemon Go from the servers supporting the app at the Apple Store and Google Play, potential users are queuing. Those in queue are making smart decisions, as many users who have opted to go to third-party servers to download the app without waiting. The researchers at Proofpoint have found versions of the Android version of the Pokemon Go app which have been modified to include “malicious remote access tool (RAT) called DroidJack.” Proofpoint goes on and notes, that the attacker is given virtually full control over a victim’s phone. How can you prevent this additional bonus RAT being a part of your Pokemon Go experience, don’t side-load (load the app from third-party sites) and wait until it is available via the Google Play or Apple Store.
Social Engineering – Pokemon Go location manipulation
A number of media outlets have carried the report out of Missouri about a gentleman who was playing the app and as he walked through a neighborhood to pick up the desired artifacts, he found himself having walked into an ambush and was robbed. The police department reported that four individuals manipulated the app player into their lair; Snopes, however, carries a comment from “the individual robbed” who said while he had the app on his phone, he believes he was robbed because he went into the wrong neighborhood.
The app relies a great deal on the location information of your device being shared with the app. In addition, the app itself allows users to create locations for players of the app to go to a given location to collect artifacts (this capability is what gave the Missouri robbery legs).
Combine the creating of the “Poke-stop” location with the ability to monitor a player’s whereabouts, one can quickly see how an individual may be induced to a specific locale; or a locale may be overwhelmed with players seeking the prize located within their establishment or facility.
Advice coming from those heavily engaged in the Pokemon Go craze, hunt in groups for safety, don’t trespass into private property (even if someone has placed a nugget within an establishment) and turn off the location features of the app when you are not playing the game.