In early March 2018, the FBI issued a warrant to search the Stafford county residence of John Glenn Weed, who had previously worked within the National Reconnaissance Office (NRO) on behalf of a defense contractor. The FBI was looking for classified materials taken from the NRO during his nine years of working on classified programs. Initial reporting from CNN indicates Weed leaked the secret NRO information via an alias Facebook account in January 2017.
What the FBI found at the residence is unknown, but what they are looking for is classified materials which the former contractor had taken from the NRO some four or five years previously. Amazingly, in 2013 a prior search of this same residence recovered classified materials.
Digging into the publicly available information, including the supporting affidavit to the federal court for the search warrant, we get a better picture of what has transpired. Lessons to be learned present themselves in droves as we review the curious case of John Glenn Weed and his alleged theft of both equipment and classified materials.
Who is John Glenn Weed?
The affidavit tells us that Weed worked at the NRO for a defense contractor from 2003 to 2012. His work at the NRO was terminated when his security clearance was pulled for cause. According to Weed’s LinkedIn profile, he worked as a senior systems architect for the Tactical Dissemination Network supporting the intelligence community special communications initiatives. He goes on to note that his work included “witting and unwitting asset tracking and surveillance; tagging, tracking and locating; data infiltration and exfiltration; over-the-horizon multimedia exploitation; mobile device application design and development; GLOWFIST Protection Level 5 (PL/5) controlled interface design, deployment and operations support.”
His profile goes on to enumerate numerous awards received while working with the NRO, to include the NRO’s Director’s Award.
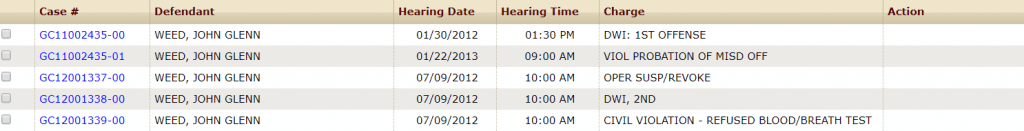
On his way to and from NRO Headquarters in Chantilly, Va, one might assume that Weed made the one hour commute each day through Fauquier County from his residence in neighboring, rural Stafford County, Va. The affidavit tells us—and Fauquier county court records confirm—that Weed had multiple DUI offenses in 2012 in Fauquier County. These events lead to the finding that he should not be allowed access to classified materials.
Duty to self-report
All who have been granted a security clearance and enjoy the trust of the U.S. government know the requirement exists to self-report any adverse information, including arrests by local law enforcement. The affidavit tells us that as part of his periodic reinvestigation, Weed omitted reporting his arrest, and only did so after having pleading guilty in the Fauquier court, some months later.
When interviewed in September 2012, by the background investigator, Weed brought with him a photo of the arresting deputy which was riddled with bullet holes. Weed had used the photo for target practice and noted his intent to “ruin the life” of the deputy.
As a result of the periodic investigation, the recommendation to revoke Weed’s clearance was made and in November 2012. His security clearance was revoked and his work at the NRO concluded. Weed appealed the decision to revoke his clearance and the appeal was denied. During the appeal process, Weed submitted a letter, which was subsequently determined to contain classified information up to the SECRET/SCI level. It was a clear indication Weed had classified materials in his possession.
Did the NRO telegraph a termination?
The affidavit goes on to explain that in September 2012, Weed conducted four “remote desktop protocol sessions” on his NRO computer to an external IP address (subsequently determined to be associated with Weed’s Stafford county address). The NRO’s investigation of the incident in May 2013 (when the events were discovered, some six months after Weed was terminated) showed that information exfiltrated out of the NRO was both compressed and encrypted. Meaning, the NRO did not know what Weed had downloaded to his personal computer at his residence. They would investigate.
First search of Weed’s residence in 2013
In 2013, the FBI, as a result of the aforementioned exfiltration of information from the NRO, searched Weed’s residence. They discovered that not only had Weed sent classified information to his residence, but he had also had given himself some high-end parting gifts, including a $200,000 radio set which had been given to NRO by another government agency, and 11 “friendly force trackers.” Based on Weed’s LinkedIn profile description of, “witting and unwitting asset trackers,” we see these items as related to his work. In all, the FBI/NRO reportedly valued the equipment recovered during the search at $340,000.
The computers and media seized during the search showed that Weed had copies of material classified at the SECRET/SCI level on projects which he had been involved during his period of contract employment supporting the NRO.
There is no record of a prosecution of Weed after the incidents of 2012 and 2013. Perhaps DOJ and NRO were happy to get their equipment back and secrets recovered.
Embers burn slowly, but ignite
Clearly Weed was doing a slow burn. In the spring of 2017, NRO was notified that someone using the name William Amos was posting classified NRO information on Facebook. A subsequent review showed that in January 2017, NRO classified information, information which Weed had worked on during his tenure, was being posted and shared on Facebook.
It was determined that Weed had created an alias account, William Amos, for the purpose of re-engaging with former colleagues. The Facebook postings indicate that apparently the search of 2013 didn’t recover all the classified materials squirreled away by Weed. The FBI opened an investigation and levied search warrants on Facebook and Comcast. Facebook shared the contents of the Amos’ accounts postings and his private messages to the FBI. Comcast confirmed the IP address used for the Amos account was associated with Weed and his Stafford county address.
The judge signed the search warrant on March 7, 2018.
Now we wait for, as Paul Harvey would say, “The rest of the story.”
Questions remain
- Why wasn’t Weed prosecuted for theft in 2013?
- Why wasn’t Weed prosecuted for retaining classified materials 2013?
- Why did the NRO’s data loss protection program take six whole months to detect the remote connections that were made in 2012?
- What was recovered in this second search of Weed’s residence?
- Will DOJ prosecute Weed this time around?
Perhaps these questions will never be answered.