Once again, an individual with access to Top Secret information broke trust and shared information with media, none of whom enjoyed the necessary need to know or authorization. Daniel Hale followed in the footsteps of NSA contractor Reality Winner and FBI special agent Terry Albury who both shared classified information with the Intercept.
In the case of both Winner and Albury, we saw how the media outlet used their information, and effectively revealed their misdeeds as evidenced by their subsequent prosecution. Therefore it is not surprising that Hale finds himself facing a multiple-count indictment for retaining, sharing, and disclosing classified information to an unauthorized person/entity – The Intercept.
Who is Daniel Hale?
Daniel Hale was originally arrested in May 2019, but the court sealed all records until yesterday, when we learned that Hale was enlisted in the United States Air Force. Hale served in the Air Force from 2009-2013, he was a language analyst. He was deployed to Afghanistan in 2012 responsible for “identifying, tracking, and targeting threat networks and targets.” In addition, he served with the National Security Agency. Following his active duty, Hale went to work for a defense contractor, Leidos, and worked within the National Geospatial-intelligence Agency (NGA), as a “Political Geography Analyst” from 2013-2014.
What Hale shared with The Intercept
Hale used his “unclassified NSA work computer” to communicate with a reporter of The Intercept in April 2013. Hale met the reporter (who media has identified as Jeremy Scahill, a founder of The Intercept) at a book signing in Washington, D.C. Following the event and introduction to Scahill, Hale used conducted searches using his Top Secret NSA computer on topics about which Scahill had written in his book, “Dirty Wars.”
By Hale’s own words, shared in a text message to a “close friend and confidant” sent in May 2013 “Scahill wants me to tell my story about working with drones at the opening screening of his documentary about the war and the use of drones.”
In June 2013, Hale again attended a book event in Washington, D.C. where Scahill was promoting his book. Following the event, the two retired to a nearby restaurant. The next day, he sent Scahill an article which discussed Edward Snowden. Again, Hale shared his good fortune of connecting with the journalist with is close friend via text message.
Hale then initiated contact with Scahill in July 2013 via phone and email, eventually traveling to New York to meet with Scahill and two colleagues. The day Hale separated from the Air Force he sent an email to the reporter advising he would travel to New York the following week. Hale indeed did travel to New York on July 23 and 24. The day after returning, Hale provided the reporters with his unclassified resume where he identified his desire to secure a position within the intelligence community and then described his work while on active duty in the Air Force and that he retained classified documents.
Hale highlighted to the journalists his work with “payloads on remotely piloted vehicles used to support real-time kill/capture operations (1540 hours, over 200 specific missions).” On August 13 Scahill and Hale spoke over the phone and then moved their future conversations to the encrypted Jabber instant messaging platform. From September 2013 through February 2014, the two had three encrypted Jabber conversations. On February 28, Hale began his removal of documents from the NGA classified system. The six documents printed were shared with Scahill and found their way to the “Reporter’s Online News Outlet”
And that was only the beginning. All in, while employed at the NGA, Hale printed 36 documents – 23 which had nothing to do with his work, and nine which did. Four documents were duplicates. Scahill published 17 of the documents in whole or part.
Hale availed himself to guidance provided by the news outlet on how to anonymously “leak” documents.
Of those documents, 11 are identified in the grand jury indictment:
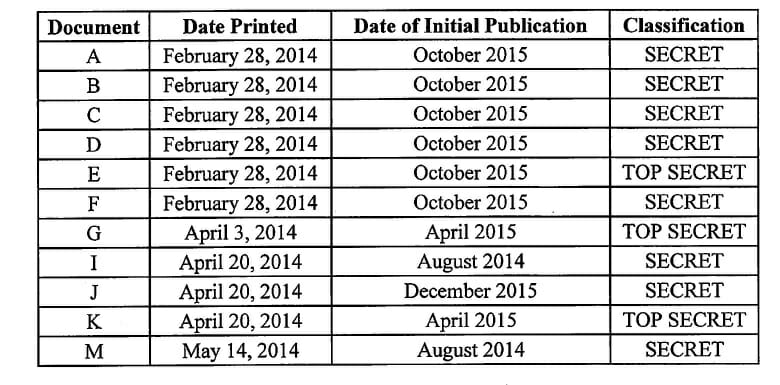
- DOCUMENT A – A PowerPoint presentation on counterterrorism operations classified SECRET//SCI
- DOCUMENT B – A document describing a military campaign targeting Al-Qaeda overseas classified SECRET
- DOCUMENT C – A March 2013 PowerPoint on military operations classified SECRET
- DOCUMENT D – A PowerPoint presentation on counterterrorism operations classified SECRET
- DOCUMENT E – Information gathered by NSA on specific named targets classified TOP SECRET
- DOCUMENT F – A PowerPoint slide outlining the effects of the military campaign targeting Al-Qaeda overseas classified SECRET
- DOCUMENT G – PowerPoint presentation outlining U.S. military technical capabilities classified TOP SECRET
- DOCUMENT I – A report listing the accomplishments of an intelligence agency tasked with preventing terrorist attacks classified SECRET
- DOCUMENT J – A PowerPoint presentation classified SECRET
- DOCUMENT K – An intelligence report on an Al-Qaeda operative classified TOP SECRET
- DOCUMENT M – Information on the Terrorist Identities Datamart Environment classified SECRET
Identifying the source of the leak
As expected, the NGA had an audit capability and the government computer systems were monitored for personnel misconduct (PM), law enforcement (LE), and counterintelligence (CI) investigations and so notified each user that such was the case. Therefore it should come as no surprise that following the publication of the documents provided to Scahill, a damage assessment and an investigation was initiated to determine the source of the leak of classified information to The Intercept who published them some months later.
Every time Hale printed a document, an audit trail was created as evidenced in the indictment. This audit trail identified the individual printing the document (Hale) and thus, the same methodology used to identify Winners was used to identify Hale – who printed the documents which have been compromised? The number will always be limited, and though it may take a bit of time to identify with precision, it is forensically low hanging fruit. The documents, their print date, their publication date, and the classification level of the leaked documents were all listed in the indictment:
What we can infer from this and prior cases is when an individual with access to classified information shares this with The Intercept, they can count on their information being used publicly and they may also count on being prosecuted. The reporter in this case used the documents provided by Hale in his book “The Assassins,” which put coin in his pocket at the expense of national security.