Once again, LinkedIn is the battleground for nation state espionage operations. Every counterintelligence and insider threat professional should be paying attention.
According to Israeli research entity ClearSky, the North Koreans targeted defense professionals (Israeli and other nationalities) by posing as senior U.S. and European defense industry professionals. The cybersecurity firm released their report, “Operation Dream Job” on August 13. The entity conducting the cyber attack has been identified as the “Lazarus Group” (aka Hidden Cobra).
Operation Dream Job modus operandi
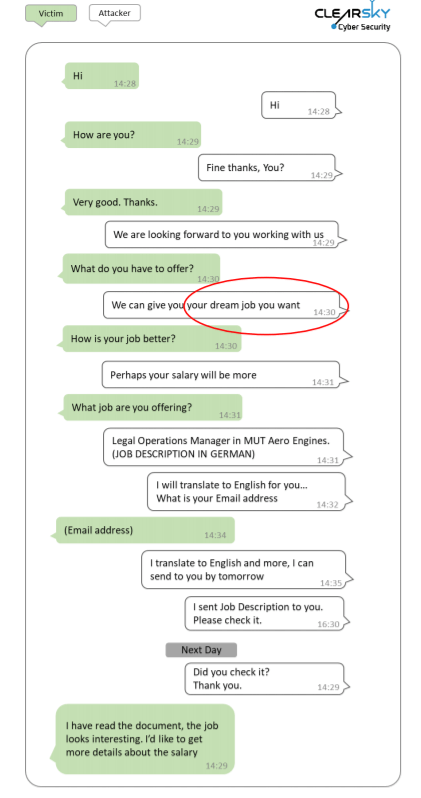
Fictitious LinkedIn profiles were created which impersonated recruitment managers associated with major global defense companies – Boeing, McDonnell Douglas, BAE. The report highlights how the group lifted and cloned entire profiles from legitimate recruiters within these companies and copied the content into their new operational profile. They then connected to “colleagues” and contacts of the authentic account for the appearance of legitimacy. The only difference between the two, the report tells us, is that the name of the fake account would have a series of numbers-letters appended to the end of the LinkedIn profile url when compared to the original.
The Lazarus Group then reached out to the selected target to initiate a discussion about a potential “dream job.” The method of contact would include LinkedIn’s in app chat capability, email, or a segue to WhatsApp and voice communications.
Check for Your LinkedIn Clone
The goal of the social engineer is to entice the target to at least take a gander at the job offering being discussed and click the attachment which is provided. This attachment carries the payload of malware designed to compromise the device and network of the target.
Once the device is compromised and the group has access to the content, their espionage goals are achieved. In the case of North Korea, they also take the extra step of compromising (as best they can) any data which permits the immediate monetization of the content, credit/debit cards, bank accounts, etc.
Following the compromise, the fake clone profile is then deleted from LinkedIn.
The operational discipline to use a profile once indicates that the group is selective in their targeting efforts – which means they are doing pre-approach surveillance and data collection. This use once and toss methodology may also mean there is a plethora of cloned and faked profiles at hand, and perhaps the counterintelligence offices in the spoofed entities may wish to have their personnel do a regular search to see if they are cloned on LinkedIn.
Lazarus Group loves LinkedIn
This is not the first time Lazarus Group has targeted personnel within the global defense sector on LinkedIn, nor should we expect it to be the last. Given the platform has little vetting of account profiles, the ability of an attacker to meld into the 837 million users is relatively risk free.
In 2017 and 2019, the group was identified as being the sponsor of “Operation Sharpshooter” which was identified by cybersecurity company McAfee. The commonality between the two operations lays in the social engineering aspect of the op. The use of fake profiles created and designed over time to present a profile which appears legitimate to a target.
Additionally, the crucial step is the attacker has the erstwhile targets engaged and their defensive briefings apparently neutralized as the victim views what they believe to be a legitimate job being discussed or offered.
If It Seems too Good to be True, It Probably Is
The temptation/need to see and read about the opportunity is too great of an inducement for the target to click – they click on the attachment. As we saw in the recent Chinese espionage case involving LinkedIn and Singaporean Dickson Yeo, the first step of the social engineering daisy chain is to engage with the perspective target – without this willful engagement by the target the attack falters at the starting gate. Don’t be lackadaisical when it comes to remembering your counterintelligence training and give these unexpected “dream job” offers a pass.