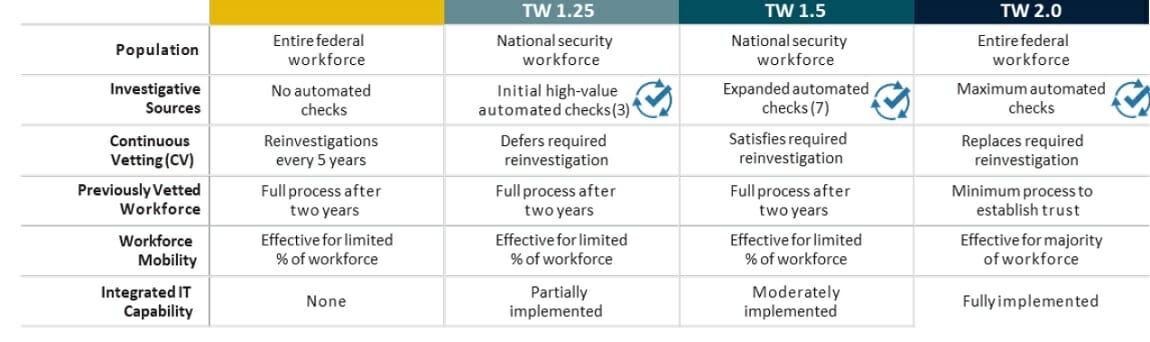
Today the Department of Defense announced all security clearance holders within the Department of Defense have been enrolled into its Continuous Vetting program, a major milestone in the Trusted Workforce 2.0 initiative. DoD’s implementation means Trusted Workforce 1.25 – its transitional effort toward full implementation – is complete. The successful implementation of 1.25 eliminates the need for periodic reinvestigations by applying a “risk-managed approach” that includes automated records checks.
“This is an incredible accomplishment and a major milestone for the national security community,” said DCSA Director William K. Lietzau. “Not only does this allow us to help ensure the trustworthiness of the national security workforce, it helps identify and address factors that may lead to insider threat incidents, all while maximizing efficiencies across government; this is a major win for the security community.”
Trusted Workforce 1.5 automates and continuously checks seven different record sources. Agencies can opt-into the DCSA CV program, or implement their own program. When Trusted Workforce 2.0 is fully implemented, all security clearance holders will be enrolled in a CV program and periodic reinvestigations will be replaced with automated checks.
Phases of Trusted Workforce
Making CV implementation possible is the government’s National Background Investigation Services, still under implementation. It’s designed to replace the legacy system inherited by the Office of Personnel Management with new, more robust IT capabilities that will enable better sharing and faster security clearance processing.
Why Trusted Workforce 2.0?
The Trusted Workforce initiative is all about enabling ongoing vetting of the clearance workforce, which will improve mobility and security. In the long term, the goal is also for the entire federal workforce to be enrolled, and not just the national security population. Under full implementation, NBIS will enable better information sharing and allow for the replacement of the traditional PR for CV.
Trusted Workforce 2.0 is anchored by a 1-3-5 principle.
One – The establishment of one personnel vetting model, which aligns guidelines and standards and provides characteristics of a trusted person. The underpinning of this personnel vetting model is changes to the federal investigative standards and adjudicative criteria.
Three – Is the reduction of the investigative tiers from 5 to 3. With the elimination of periodic reinvestigations, categories based on reinvestigation go away, and investigations are based solely on tiers of risk, not tiers of time.
Five – Is the creation of five specific vetting scenarios.
- Initial vetting: Moving ‘outsiders to insiders.’
- Continuous vetting: The ‘signature, transformative piece’ of Trusted Workforce 2.0. Continuous vetting allows for risks to be identified when they happen – not on a 5-or-10-year investigation timeline.
- Upgrade in trust: When an individual with a Secret clearance needs to move into a Top Secret clearance position, or an individual requires access to special access programs, conducting new vetting for the higher risk level.
- Transfer of trust: How quickly and efficiently to move from one agency to another. Typically referred to as reciprocity, which actually brings in a host of other criteria related to suitability.
- Reestablishment of trust: Vetting an individual who has left the ‘trusted workforce.’ Under the PR model, investigations would be considered ‘current’ if the individual attempted to ‘re-enter’ the system within two years. With PRs going away, reestablishment of trust won’t be based on an investigation date, but on what information is available in a continuous vetting system of record, and efficiently bringing those individuals back into the system.
FAQ on Trusted Workforce 2.0
HOW DOES CONTINUOUS VETTING (CV) WORK?
CV involves regularly reviewing a cleared individual’s background to ensure they continue to meet security clearance requirements and should continue to hold positions of trust. Automated record checks pull data from criminal, terrorism, and financial databases, as well as public records, at any time during an individual’s period of eligibility. Potentially derogatory information in the form of incident reports, insider threat information and other sources also feeds into the CV alert process. When DCSA receives an alert, it assesses whether the alert is valid and worthy of further investigation. DCSA investigators and adjudicators then gather facts and make clearance determinations. CV helps DCSA mitigate personnel security situations before they become larger problems, either by working with the cleared individual to mitigate potential issues, or in some cases suspending or revoking clearances.
WHAT IS NBIS?
NBIS is the new personnel vetting IT system that is transforming the background investigation process to deliver stronger security, faster processing, and better information sharing,. It will replace a suite of outdated, legacy IT systems that no longer meet the needs of the U.S. government. It is the future of personnel vetting, enabling the federal government to fully meet necessary TW 2.0 policy reforms. DCSA is planning NBIS capability deployment and onboarding/adoption in a phased approach. This gradual rollout is designed to ensure NBIS capabilities have gone through significant user acceptance testing.
ABOUT DCSA: “AMERICA’S GATEKEEPER”
DCSA, the U.S. government’s largest security organization, is the federal agency that secures the trustworthiness of the U.S. government’s workforce, the integrity of its cleared contractor support, and the uncompromised nature of its technologies, services, and supply chains through vetting, industry engagement, counterintelligence support, and education.
Learn more and connect with DCSA at www.dcsa.




