Former Air Force Technical Sergeant and Air Force Office of Special Operations (AFOSI) Special Agent, Monica Witt’s defection to Iran took the Iranian Islamic Revolutionary Guard Corps (IRGC) by surprise. In their mind, she was only an agent of influence to be rolled out when an occasional bash at the U.S. was desired. They had not anticipated Witt would be a counterintelligence bonanza.
Based on the grand jury’s indictment of Witt and contemporaneous events, we unpack the various ways Witt assisted or may have assisted the IRGC in their intelligence and counterintelligence efforts.
Monica Witt debrief prior to arrival in Iran
Whenever a walk-in arrives on one’s doorstep, the receiving intelligence officer conducts an initial debrief. The first question out of any intelligence officer worth their salt is, “Do you have information pertaining to an imminent threat?” In Witt’s case that was highly unlikely, but she did have an interesting tale to share given just three years prior she had been sitting on the desk within AFOSI working on two compartmented U.S. intelligence programs targeting Iran.
This initial debrief occurred in Kabul, at the Iranian Embassy, and continued in Dubai, where the Iranians had her travel, on their dime. They used her time in Dubai to garner additional details to determine whether or not to bring her into Iran.
Witt arrives in Iran
Witt’s arrival and assimilation in Iran has been characterized as, “They gave her a flat and a computer.” They gave her much more than that, as it has now been five and one-half years and she still is (we think) alive and well within Iran.
During this initial period of validation there is little chance they exposed to her their ongoing operations – if ever. Trust is a delicate dance, trust here but not there. If an individual voted with their feet once, they may do so again. They still had to determine what motivated Monica Witt to take such a precipitous action as to volunteer her services to Iran?
The first step would be to empty her of all information she may recall based on her ten years of service. The indictment indicates she compromised both Secret and Top Secret information, as well as information which came from special compartments HCS and SCI, to which she had been given privileged access.
Next, dissecting her professional life would take place. She would be walked through her early days as a linguist flying above the Middle East capturing signals intelligence in the RC-135 Rivet Joint reconnaissance aircraft, to her most recent role as a government contractor. She would be asked to confirm names, positions, responsibilities, SOPs, etc. Remember, Witt was able to produce, digitally, her DD214 when challenged for additional bonafides, indicating she had stored documents either on her laptop or in the cloud. These too would be reviewed, inspected and dissected in every conceivable manner.
They would also have her conduct operational tasks, many of which they no doubt had already conducted themselves. And of course, questions, thousands of questions. Like trial lawyers rarely asking questions they did not already know the answer.
Remember, the IRGC had already enjoyed a counterintelligence windfall during the period of time from 2009-2013 when they wrapped up U.S. intelligence assets due to the compromise of a covert communications system. The compromise , while it pre-dates the arrival of Witt, provided the IRGC with key data points upon which to validate Witt.
Witt’s active collaboration begins
We know from the indictment that Witt identified eight former colleagues, two who had worked directly with Witt on the two compartmented projects which Witt has been involved with both as an AFOSI special agent and as a contractor; two of whom worked with Witt in the U.S. and two who had worked with Witt abroad; one who worked with Witt in a supervisory role and the eighth who had attended (unidentified) training with Witt.
Over time her actions and the results of her actions would serve to convince the IRGC that she had utility. She became part of the IRGC’s offensive counterintelligence efforts against the United States.
From January 2014 through May 2015 Witt assisted the IRGC in the development of “target packages for use by Iran against the USG agents, including undercover counterintelligence officers.” The AFOSI defines the target package as “a document or documents assembled to enable an intelligence or military unit to find, fix, track, and neutralize a threat. A human target package includes information collected about an individual, such as the official position of the individual, an analysis of personal vulnerabilities or other opportunities to exploit the individual, and confirmation of the identity and location of the individual. Finally, a target package recommends a neutralization plan, which may include apprehension, recruitment, cyber exploitation, or capture/kill operations.”
She used a number of fictitious Facebook accounts to conduct in-application searches for the “USG Agents” collecting their personal information and providing nuance to the information. No doubt, she conducted additional open source research on identified personnel and assisted the IRGC in their creation of fictitious cyber personas. Remember, the indictment identifies four Iranian citizens, Mojtaba Masoumpour, Behzad Mesri, Hossein Parvar and Mohamad Paryar, referred to as “Cyber Conspirators.” These individuals were charged with conspiracy, attempts to commit computer intrusion and aggravated identity theft. One of these four, Behzad Mesri, has previously been indicted by the Department of Justice, for his role in the 2017 theft of Game of Thrones and extortion of HBO.
These four Iranians are specifically called out as having been instrumental in developing the malware which was served up to the targeted individuals designed to “capture a target’s keystrokes, access a computer’s web camera, and monitor computer activity.”
Within 15 months of Witt’s arrival in Iran, the Iranians were utilizing her knowledge in an active offensive counterintelligence campaign designed to provide “persistent access to the recipient’s computer and network.”
The IRGC was now executing their cyber-espionage plan of action.
Bella Wood: Spear Phishing Attack
The Cyber Conspirators built infrastructure outside of Iran to conduct their cyber ops. They created fictitious personas, one identified persona was that of “Bella Wood.”
Bella Wood successfully engaged one of Witt’s former colleagues with direct knowledge of the special compartment programs which had now been compromised by Witt. The wording of the spear phish email sent to this individual seems to indicate that Witt was not directly involved in the crafting of the verbiage, as the verbiage provided in the indictment is not that of a well-educated, native English speaker. A second spear phish email contained preposterous instructions to “deactivate your anti virus to open.” The targeted individual did not click on the links or attachments in either spear phish email. The Bella Wood persona failed.
They weren’t done.
Imposter Accounts
The Cyber Conspirators, using Witt’s targeting package opted to create a duplicate Facebook account in the true name of one of Witt’s former colleagues who had worked with her in the United States. They reached out to another of Witt’s former colleagues with direct knowledge of the special compartmented programs and connected via Facebook. Wasting no time, that same day they sent a message to the U.S. government agent which contained an attachment with a malware payload attached. This individual did not open the zip-file attachment. When that failed, the same account reached out to additional USG accounts with attempts to connect and provide attachments to be opened by the targets. By May 2015, the imposter account had been identified as such and this aspect of the offensive operations fizzled out and this too failed.
No doubt the coincidence of the number of individuals, associated with AFOSI, many of whom were themselves counterintelligence officers did not go unnoticed.
The dots were connected in May 2015 and the centerpoint no doubt pointed to their former colleague Monica Witt who had fallen off the planet in the summer of 2013.
Is Monica Witt finished collaborating?
The visibility into Monica Witt’s role in aiding and abetting the Iranian IRGC in their offensive efforts ends with the indictment end date, May 2015. It is highly unlikely that Monica Witt’s collaboration ended.
While the Bell Wood persona failed against trained intelligence officers, and the duplicate or imposter persona is now a regular occurrence for every user of Facebook, the IRGC did not stop. Indeed they showed their professional acumen by evolving their tradecraft and techniques.
How much of that involved Witt?
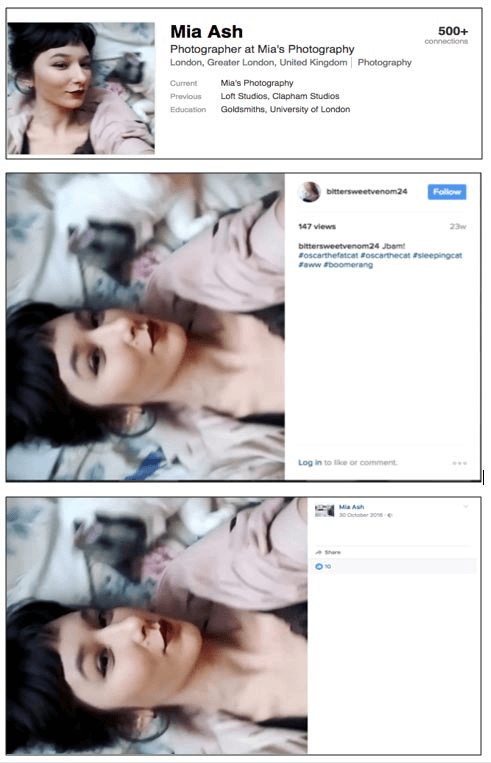
For example, in 2017 the IRGC created a highly successful use of the fictitious persona, “Mia Ash”. Mia Ash was used in targeting, assessing and engaging individuals of interest within targeted organizations on a global basis. The IRGC had reiterated their social engineering skills and taken it up a notch.
Mia Ash set up shop on LinkedIn, and this time a comprehensive backstory was created to support the persona. This, and a pretty face, was apparently all the entre needed to engage with targets across a multitude of countries and industrial sectors.
Then in March 2018, we saw the Department of Justice indict nine Iranians who successfully compromised insiders and stole the intellectual property and sensitive data from both private and public entities. These nine penetrated, “144 U.S. universities, 176 universities across 21 different countries, 47 domestic and foreign private sector companies, the U.S. Department of Labor, the Federal Energy Regulatory Commission, the State of Hawaii, the State of Indiana, the United Nations, and the United Nations Children’s Fund.”
What connection is there to Monica Witt? This activity by the IRGC began in late-2013.
Who still believes in coincidences?
In time we may learn more about Monica Witt and her activities on behalf the Iranian intelligence, suffice it to say:
- She put a number of U.S. clandestine intelligence officers at risk.
- She compromised operational activities about which she had first hand knowledge targeting Iran.
- She provided knowledge which led to the compromised and arrest of assets working against Iran.
- She assisted the IRGC in their cyber espionage campaigns.
- She remains a resource to the IRGC offensive operations and their propaganda machine.
She wished to do damage to the United States, and she is.