Better than simply wondering if you fall under the Department of Defense (DoD)’s Continuous Evaluation (CE) program, it’s always better to arm yourself with the facts. CE went into effect October 2014, carrying out the Secretary of Defense’s March 2014 recommendation.
DoD has implemented its CE program in a planned and phased approach, increasing the number of cleared individuals enrolled over time. How many are in the program and who will be eligible? DoD reports the following:
- Initial pilot of approximately 100,000 military, civilian, and contractor clearance holders
- 225,000 total in December 2015
- 500,000 total in December 2016
- Estimated 1 million by December 2017.
- Department goal to enroll all DoD clearance holders by the end of fiscal year 2021
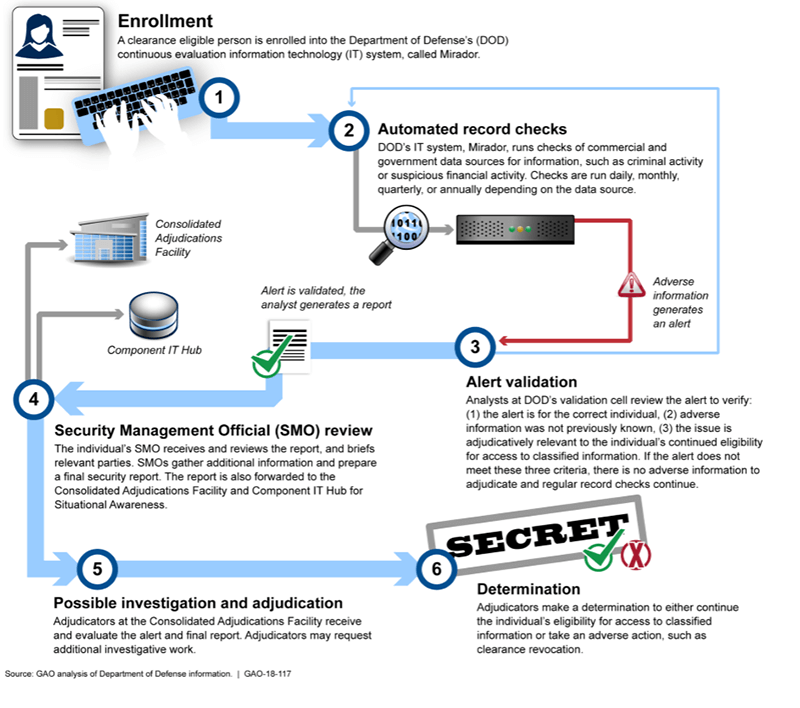
Mirador, which is a separate IT system from what ODNI is developing to implement CE, is the name of DoD’s own continuous evaluation IT system. The system conducts automated record checks of commercial and government data sources on enrolled DoD members. The goal of the automated checks is to provide near real-time identification of adverse information to be added to considerations used during the evaluation of a clearance holder’s ongoing eligibility for access to classified information. Despite Mirador already being in use, the system is still under development. Mirador is expected to be fully operational by fiscal year 2018.
The Continuous Evaluation Process
How does it work for those who are in the system? It all begins with the automated checks. Once an alarm is sounded on a clearance holder within the system, it’s immediately checked to ensure the information is credible, has flagged the right person, whether or not the issue has already been previously recorded, and if the information is relevant to the adjudication process.
If an analyst reviews the alert and finds the incident is valid, new, and relevant, a report will be generated and sent to the candidate’s security manager. All alerts are prioritized based on severity of the incident and the reports are reviewed and approved by a supervisor before forwarding to a security manager. If any additional investigative work is required, adjudicators will be the ones to determine the candidate’s continued eligibility for a security clearance. Clearance holders still have access to due process safeguards during periodic reinvestigations.
The reality is that if you have an incident, you will either need to report it now or wait for it to come up during your reinvestigation process. The goal of continuous evaluation is to flag incidents sooner and resolve them with either a revoked clearance or updated information in the system.
“We hope to eventually reach the point where through the use of CE, we can eliminate the need to do secret-level reinvestigations,” Daniel Payne, the director of the Defense Security Services said. “We also want to identify those employees at the top-secret [level] who we need to do earlier in the process and reduce the wait time to get a top-secret clearance done.”
So what are the results of the CE program? As of February 2017, DoD has reported the following:
- 12,400 alerts received by the system that checks about 22 different databases throughout the DoD, the U.S. government and the private sector
- Out of 12,400 alerts, only 2,064—applicable to 1,816 individuals—were determined to be valid, relevant, and new
- Action was completed on 1,307 of those cases
- 859 cases were closed with a favorable decision, but context was added to the individuals’ records
- 375 cases the subject separated and/or no longer needed access
- 62 cases involved a clearance revocation, condition, or warning.
Based on the metrics to date, DoD’s CE program helped to identify risk, on average, 6 years 7 months sooner than the traditional 10-year periodic reinvestigation model for secret -eligible clearance holders. And for Top Secret-eligible clearance holders, the CE program identified issues 1 year 5 months earlier. Going forward, the DoD plans to find a way to automate the metrics process.
While it may be a pain to implement CE in conjunction with insider threat initiatives, the value of identifying threats sooner is not to be ignored. The benefits of a cohesive program outweigh the inconvenience. However, time will tell if CE is implemented in a cohesive manner across the agencies that actually identifies real threats without creating added headaches to hard-working civilians, military personnel, and contractors.