On July 24, Jun Wei Yeo (aka Dickson Yeo), a Singaporean living in Washington D.C., pleaded guilty for actively recruiting intelligence sources on behalf of China’s intelligence apparatus (People’s Liberation Army – PLA and Ministry of State Security – MSS). Yeo took advantage of the LinkedIn algorithm to aggressively target and build contacts for Chinese intelligence. He used a fake consulting company to solicit and engage intelligence targets, and the LinkedIn platform made it easy.
Dickson Yeo’s Guilty Plea
The Department of Justice (DOJ) accepted Yeo’s guilty plea to one count of not registering as an agent of a foreign power, as per the Foreign Agents Registration Act (FARA). In his plea, Yeo provided details on the modus operandi used to both recruit sources and to communicate with China. As expected, the guilty plea does not contain the totality of the five-year relationship between Yeo and China (2015-2020).
“Today’s guilty plea underscores the ways that the Chinese government continues to target Americans with access to sensitive government information, including using the Internet and non-Chinese nationals to target Americans who never leave the United States,” said Michael R. Sherwin, Acting United States Attorney for the District of Columbia.
YEO’s fake company, fake jobs, lead to real connections
The court documents are particularly noteworthy and relevant to all Facility Security Officers who are maintaining counterintelligence and insider threat programs.
Yeo was instructed in 2018 by Chinese intelligence operatives to create a fake company and use job boards to find potential “consulting” candidates by posting fake jobs. Yeo created “Resolute Consulting” (NB: not associated with the IT consulting, Resolute Consulting Group of Houston). He then slapped together a website (reso(dot)rocks) in which he placed a link to his LinkedIn profile, gmail account, and a Singapore mobile number as contact information. On his web page, he explains how his Resolute Consulting was “formed as a result of a brain-storm between multiple parties in Singapore and Shanghai.” He omitted that he was the only Singaporean participant and that the Shanghai participants were Chinese intelligence. He then began posting jobs on internet job boards and expanding his social network on LinkedIn.
LinkedIn Harvest Coupled with 2015 OPM Data Breach Equaled a Treasure Trove
Yeo told investigators, “he received over 400 resumes,” he continued, “90% of the resumes he received were from government personnel with security clearances.” Yeo would pass the more interesting resumes on to his Chinese intelligence officers. Chinese intelligence officers likely reviewed the candidate’s portfolio, including OPM data breach information, as well as other data breaches, for additional assessment information.
His LinkedIn harvest of contacts was especially bountiful. Yeo explained how he felt like he was addicted to LinkedIn, as every day their algorithm would suggest to him new potential targets for him to contact. After making initial contact, Yeo would attempt to have the target enter a commercial relationship with his firm and provide written reports. His Chinese intelligence handlers trained Yeo on how to elicit information from his potential targets in order to identify those who were “dissatisfied with work, were having financial troubles, had child support” and developed good rapport with Yeo.
Yeo’s Successes Inside the U.S.
Yeo relocated to Washington D.C. from January-July 2019. His LinkedIn profile claims he is an adjunct senior consultant for KWR International, specifically Keith Rabin. We reached out to KWR International for comment and have not yet received a response.
The time in Washington D.C. was used to troll for targets within the Beltway ecosystem of consultants, think tanks, lobbying firms, and defense contractors. While the exact number of individuals who entered into a commercial relationship with Yeo is not provided in the court documents, there are some noteworthy examples of individuals with access to sensitive/classified information:
- An individual working on the United States Air Force F-35B military aircraft, who U.S. law enforcement confirmed had a high-level national security clearance. This individual told Yeo he was having financial difficulties. Yeo had this individual write a report on the “geopolitical implications of the Japanese purchasing the F-35.”
- An officer within the U.S. Army whose duty station was the Pentagon. This individual told Yeo he had been traumatized by his multiple tours in Afghanistan. Yeo tasked him to write reports for “Korea and other Asian Countries.” The officer wrote on “how the withdrawal of military forces from Afghanistan would impact China.”
- A State Department employee who confided to Yeo that he was dissatisfied at work and had financial difficulties. Yeo had him write about a “member of the U.S. cabinet.”
Yeo’s Reach Outside the U.S.
It would appear that Yeo’s targeting assignment may not have been limited to the United States. Yeo’s LinkedIn profile contained a number of “recommendations” from international colleagues who had a relationship with Yeo.
One individual, ostensibly from Norway, indicated that in mid-2018, Yeo was “professional, timely, and precise in describing the client’s objectives and showed amazing follow through from project specification to delivery.” The comment from this individual identifies Yeo as a “political risk advisor in SE Asia.” This individual was contacted, responded, but declined to provide details on his engagement with Yeo.
Meanwhile in Singapore, an individual who attended the Lee Kuan Yew School of Public Policy at the National University of Singapore with Yeo, noted, “Dickson is also highly motivated and entrepreneurial as evidenced by the consulting business he has built at the same time as doing his PhD.” This individual has not responded to our request for comment on Yeo.
China’s covert communications regime used with Yeo
China, ever vigilant of the counterintelligence arm of the U.S. intelligence and law enforcement community, used rudimentary procedures to reduce the likelihood their communications with Yeo would come to the attention of the United States.
- Yeo was instructed to not travel to the U.S. with his phone or notebooks.
- Any email from the U.S. from Yeo should not occur unless he was connected to the internet at a coffee shop.
- Device-to-Device communications used the encrypted Chinese messaging application, WeChat. He was also directed to create a new WeChat account every time he connected with his Chinese intelligence handler and to use multiple phones.
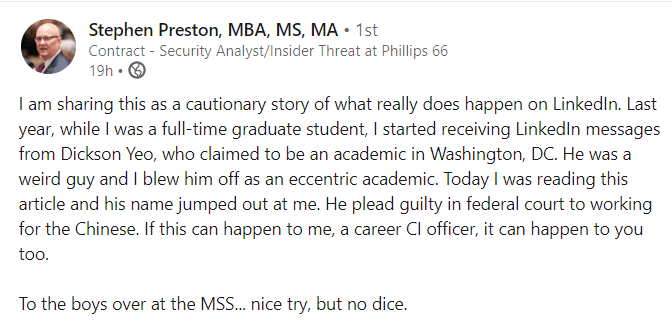
First person account
Stephen Preston, retired U.S. Army counterintelligence officer posted a cautionary story on LinkedIn. Preston, in late-2018 was contacted by Yeo. Preston was engaged in full-time graduate studies at Rice University at the time. He described Yeo as an “eccentric,” a person’s who manner was unpolished and stilted.
Social networks Are Key Targets
This is not the first instance of China (or any intelligence organization) using social networks to spot, assess, develop, and ultimately recruit sources of sensitive/classified information. Kevin Mallory is a prime example. He was recruited after being contacted via LinkedIn by Richard Yang, who was acting in a similar role as Yeo on behalf of Chinese intelligence.
In the aforementioned examples, the hooks were set with the individuals crafting seemingly innocuous commercial reports and providing these to Yeo with a remuneration of $2,000 for each. The U.S. Army, State Department, and the Air Force civilian employees will be hard pressed to explain their engagement to their employers. Court documents show Yeo was instructed to move the U.S. Army officer from the commercial engagement to providing to Yeo U.S. classified information. Yeo was arrested before that happened.
Caution is the counterintelligence watchword
In May 2018, we didn’t know about Yeo, but we did know about Mallory’s Yang. We provided the following advice then and repeat it today.
Individuals who enjoy the trust of the United States should be hypersensitive about falling within the targeting pool of the PRC or any other hostile intelligence organization. You, the individual, do not choose whether or not you are a target. The adversary makes that decision. Report all foreign contacts and inquiries to your security office.