All who have followed the machinations of Iran over the past 40+ years know that the enmity towards the United States has not diminished one iota. In recent days, we learned of the Iranian government apparently planning an assassination of a senior U.S. diplomat and the targeting of former State Department personnel via LinkedIn.
Iran Plot to Assassinate?
Politico broke a story on September 13, apparently leaked from the State Department which indicates that in retaliation for the assassination of Iranian Revolutionary Guard Corps commander Soleimani on January 3, the Iranian government is targeting U.S. Ambassador to South Africa, Lana Marks for assassination. The threat to Marks was identified in early spring 2020, and she was warned.
Marks, who was born East London, South Africa is a political appointee, better known for building a successful high-end handbag design company than diplomacy, presented her credentials to South African President Cyril Ramaphosa on January 28. Unnamed sources speculated that Marks was targeted given her personal relationship with the U.S. president.
Critics note the timing of the anonymous source from within the U.S. government coming forward with dated intelligence on Iranian activities should be viewed through a political lens. This is not the first time Iran has allegedly targeted U.S. personnel for assassination, nor will it be the last given the current state of affairs.
Iran targets via Social Networks
Separately, cybersecurity firm ClearSky published a report “The Kittens are Back in Town 3” which details Iran’s use of spear-phishing with popular social networks: WhatsApp and LinkedIn. In this instance, the Iranians impersonated known journalist and their LinkedIn accounts. The report identifies German “Deutsche Welle” and “Jewish Journal” as the two main media entities used by the Iranians.
When the “Charming Kitten” malware was first identified in 2014, it was used mainly to target academics. The most recent revelation provided by ClearSky indicates that high ranking members of the U.S. government and former employees of the State Department are included in the Iranian targeting matrix.
In January 2020, the researchers discovered the Iranians were willing to engage their targets via audio chat using the WhatsApp calls from legitimate German phone numbers. This operational act, the report notes, is not the first time WhatsApp audio calls have been used, as detailed in the most recent use of LinkedIn by the North Koreans.
The 2020 hook used, was the request to participate in an “online webinar/meeting” about Iran and subjects of apparent interest to the targeted individual. The Iranians introduced themselves as established and verifiable journalists (impersonating the real journalists’ LinkedIn accounts) and with the invite, the bait was:
- A full list of other participants
- Date and time of Webinar (via Zoom)
- Details regarding the payment for attending the Webinar
The social engineering approach began with email, then attempts to segue to WhatsApp. ClearSky continues how if the target is hesitant, the attacker will send a link to the fake LinkedIn account.
LinkedIn will remain a hostile intelligence officer’s dream tool as long as targets of interest continue to utilize the social network.
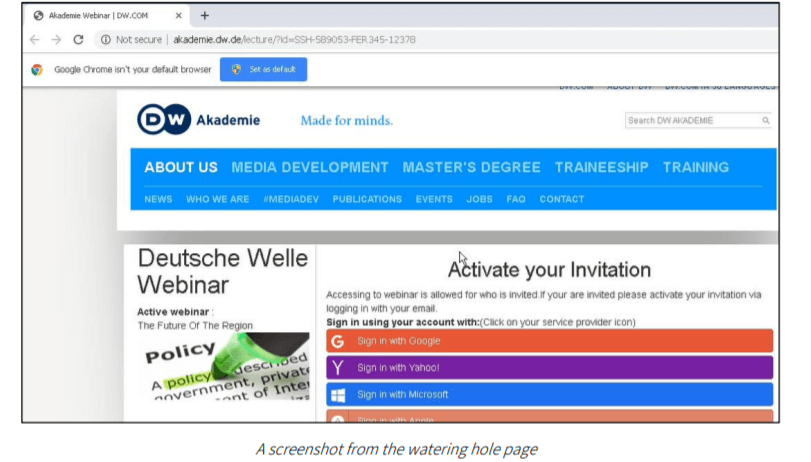
The link which hosted the malicious payload was in fact a Deutsche Welle web page which had been previously compromised and under the Iranian’s control.
Given the timing, it appears coincidental that the targeting of U.S. government employees and former State Department employees began in January 2020, contemporaneously with the presentation of Ambassador Marks credentials to the Government of South Africa. There is no evidence that these two events are related beyond being attributed to Iranian intelligence entities.
Take Away for the FSO
Exemplars of both the email exchanges and the WhatsApp exchanges are provided in the ClearSky report and Facility Security Officers should avail these to their constituents so the cleared employees may recognize the modus operandi when it is their turn in the Iranian targeting barrel.
Furthermore, Deutsche Welle was the unwitting vehicle by which the Iranian’s managed their operation. This should sound the klaxon loud and clear that the security of all domains and web pages is paramount, or your entity could be the next host of a nefarious operation.