The United Kingdoms’ Centre for the Protection of National Infrastructure (CPNI) in conjunction with the counterespionage components of the UK’s National Security Service’s (MI5) once again highlight to the UK’s governmental workforce the danger to those using LinkedIn presented by hostile nation states via a “Think before you link” counterintelligence campaign.
The campaign and warning being pushed out to over 450,000 UK civil servants and members of industry and academia carried with it the ominous news that over 10,000 in UK government, business and academia have been targeted within the last five years. We know the UK has been tracking the operational use of LinkedIn, as it was the MI5 who sounded the claxon on the use of LinkedIn for targeting, contacting, engaging, assessing, and ultimately recruiting sources from within the UK government by hostile actors back in 2015.
counterintelligence awareness Global Concert
This counterintelligence awareness campaign is made in concert with those of other allied nations. The United States created and launched a similar campaign in September 2020, the “Nevernight Connection.” Following that, Australia launched their campaign targeting the use of LinkedIn with their own “Think Before You Link” campaign in November 2020. Both had been preceded in 2019 by the FBI’s Office of Private Sector (OPS) who issued an explicit warning to the private sector on the threat posed by social networks.
If one needs further evidence, we don’t have to look too far back in our collective counterintelligence memory, to see how in 2018 the government of France warned their governmental workforce of the use of “consulting contracts” and “fake interviews” which touched over 4,000 French workers. This had been preceded by the German BfV’s warning in 2017 and again in 2018 that over 10,000 Germans had been successfully contacted via LinkedIn with dubious offers of engagement.
Google reminded us twice this year about the efforts of North Korea to target security researchers, and we saw Iran use the platform to great effect in 2019.
Yet the U.S. cleared workforce need not look abroad for definitive evidence of the use of LinkedIn by China and other hostile intelligence actors. The case of Dickson Yeo (2020) who was addicted to the level of success he was enjoying on behalf of China as LinkedIn’s algorithms provided him with lead after lead.
And then we have the malevolent insider, Kevin Mallory (2018), who was recruited via LinkedIn and went on to become a most collaborative asset. He is joined by Ron Rockwell Hansen (2019), also a malevolent insider, who not only attempted to provide intelligence, he also took part in the spotting, assessing and engaging his former colleagues within the intelligence community on behalf of Chinese intelligence.
At the risk of being repetitious, China uses LinkedIn for espionage.
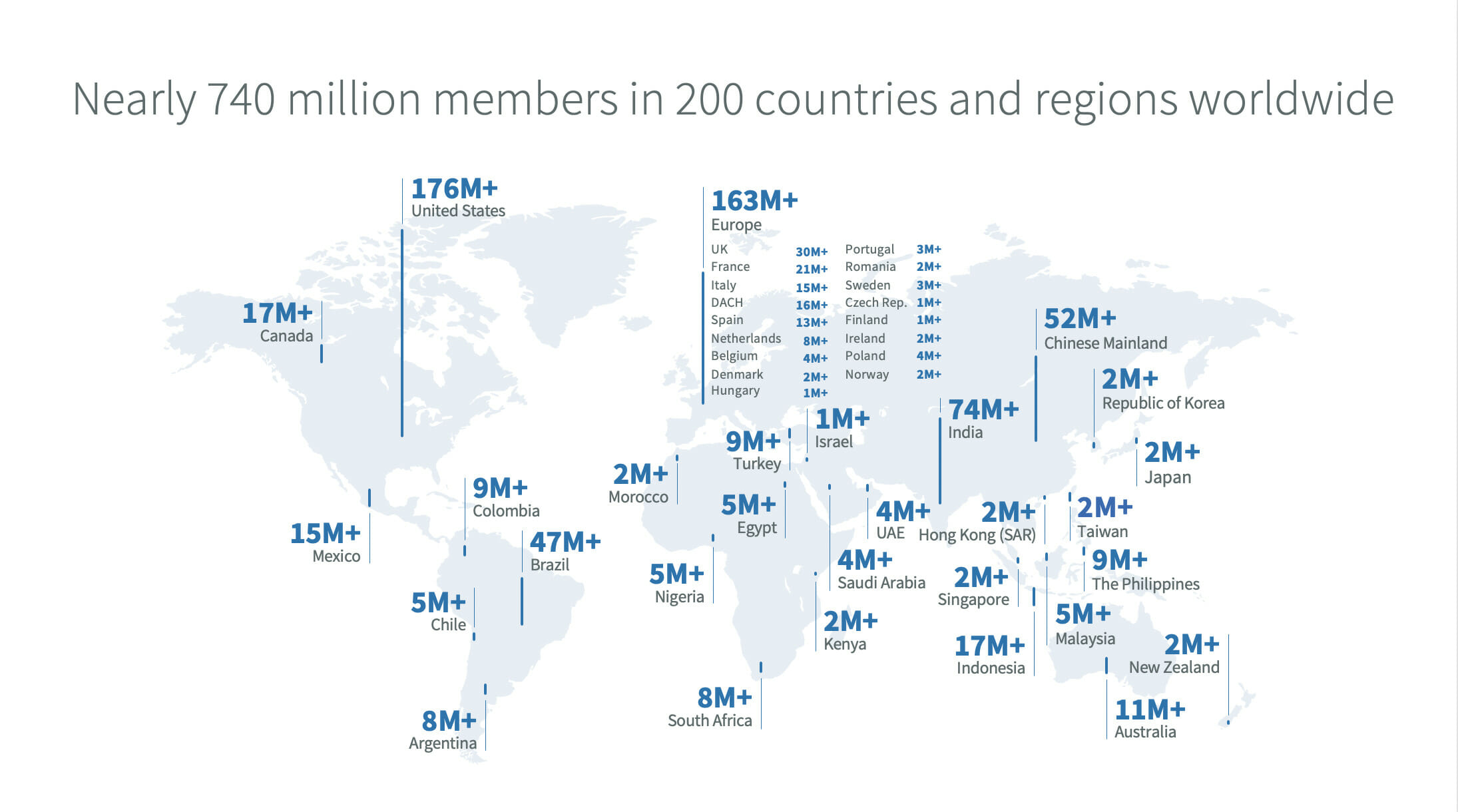
According to LinkedIn’s map, there are over 722 million LinkedIn users, of those 171-plus million are in the United States and 30-plus million in the United Kingdom, according to LinkedIn. How many in China? A mere 52-plus million, of which we have already determined some are up to skullduggery on behalf of government of China.
What’s LinkedIn doing? Their efforts are noble but insufficient. Paul Rockwell head of trust and security at LinkedIn is quoted by the UK’s Financial Times as noting that his staff actively sought signs of “state-sponsored activity” and removed fake accounts using intelligence from a variety of sources, including government agencies. In the first six months of 2020 LinkedIn had removed 33.7 million fake account registrations. No data is provided for the second half of 2020, nor for the first quarter of 2021.
Why is this counterintelligence message seemingly repeated ad nauseum?
It’s repeated every year because individuals with access to information of interest to hostile actors continue to make themselves available via social networks, including LinkedIn. This availability in and of itself is not where the risk lays. The risk lays in what does the individual share to potential employers and collaborators via their LinkedIn page and how do they engage with those who may approach them.
As has been said many times, one does not get to choose whether or not they are a target of a hostile intelligence entity, the adversary makes that decision. What the individual, their FSO, and their employer can do is prepare the individual for the approach and arm the individual with the counterintelligence tools necessary to joust and deflect with the hostile intelligence officer.
Take a look at the UK’s “Think before you link – Glitch” video prepared by the CPNI as part of this campaign.