Do you love going down the rabbit hole to find that next critical piece of information? Do you surf the deep and dark web waves? When you find a piece of string do you rip it, or pull it until you get to the source? Here, on this episode of ‘Diving into the Disciplines,’ we’ll take a look at the intelligence professionals who scour the web for open source secrets – also known as open-source intelligence, or OSINT.
What is OSINT
Of all the intelligence disciplines, OSINT is probably the most widely used in both national security and the private sector for obvious reasons: it is easily retrieved and exists in the public domain. U.S. law defines OSINT as data produced from publicly available information that is collected, analyzed, and disseminated while addressing a specific intelligence requirement.
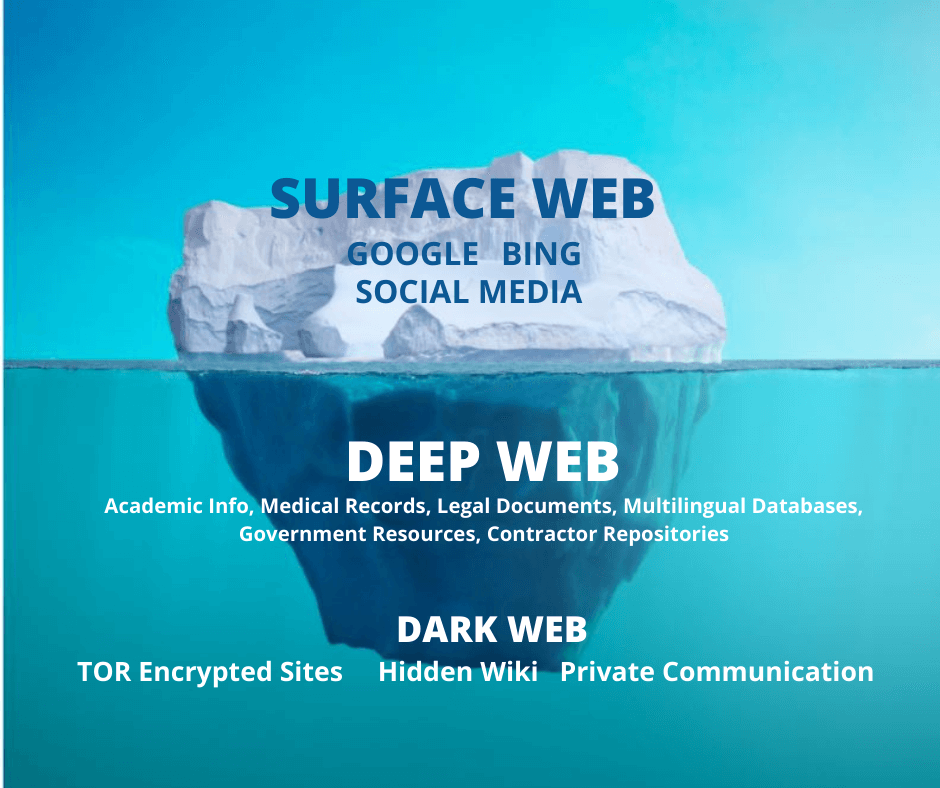
OSINT has been prevalent for years, but has become even more important since the onset of COVID-19. With analysts working outside of the SCIF, sometimes OSINT is the only option. Just because it’s public, doesn’t mean it’s easy to find. The surface web – the kind of information gathered with a basic Google or search engine, is just one aspect of OSINT.
Diving Deeper on the Web
OSINT Analysts also retrieve information from the deep web and dark web. The deep web refers to non-indexed pages, while the dark web refers to non-indexed pages that are involved in illegal activity – mainly content that resides on darknets and overlay networks that require a certain software or configuration to view.
While OSINT is valuable, the hazards of overwhelm and misinformation are high. A key drawback to searching in the public eye is that whatever can be found by cleared intelligence collectors can also be found by adversaries. This is always why all-source intelligence is the best way to analyze a system, person, or event.
OSINT Analyst Requirements
While OSINT is performed on the public web, most of the tools are government or contractor owned to avoid foreign adversaries attacking the networks holding the data. And it’s why most OSINT analysts still require a security clearance in order to do their jobs effectively.
While OSINT sources are used in a number of the intelligence disciplines, a traditional OSINT analyst will be cruising the world wide web in search of information to support intelligence reports. Because foreign adversaries are often the topic of these reports, having a second language under your belt will usually give you a leg up on the candidate competition.
If you’re not afraid of the dark – web that is – and you have an eye for detail, consider career opportunities as an OSINT analyst, and check out some of the in demand OSINT skills defense contractors are seeking at ClearanceJobs.com.