The recent GAO report “PERSONNEL SECURITY CLEARANCES”, Plans Needed to Fully Implement and Oversee Continuous Evaluation of Clearance Holders” outlines the missed milestones and continued delays for implementing the government-wide continuous evaluation (CE). In conjunction with the initiation of the security clearance reform efforts to modernize personnel security processes and improve the timeliness and quality of investigations, CE was to be a key component in helping fill information gaps associated with the time between periodic reinvestigations (PRs). So, do these delays have a real impact to our national security? You decide.
In the fall of 2013, following the Washington Navy Yard shooting, the President directed the Office of Management and Budget (OMB) to conduct a review of the Federal employee suitability and contractor fitness determinations, as well as security clearance procedures. Brief history, at the time of the Sept. 16 2013 Navy Yard shooting, Aaron Alexis, who held a secret security clearance, was not due for a reinvestigation until June 2017 (initial investigation closed 2007).
Throughout Alexis’ period of access, he routinely demonstrating very troubling and escalating misconduct (traffic tickets, insubordination, disorderly conduct, multiple unauthorized absences from work, and criminal arrests), and had received administrative/non-judicial punishments. The most egregious conduct demonstrated by Aaron Alexis leading up to the Navy Yard shooting occurred on August 10, 2008, and September 16, 2010. Respectively, Alexis was arrested twice, once for disorderly conduct, and the other for unlawfully discharging a firearm. Even with the “documented” and growing history of arrests and significant character and conduct issues, Alexis remained in access until that tragic day when he killed 12 people at the Washington Navy Yard.
In May 2014, the 120-day review was released presenting a set of recommendations that would “establish a new set of priorities for security clearance reform, while accelerating efforts already underway”. The priorities included improving access to relevant information, especially state and local law enforcement records; accelerating the shift to a continuous evaluation model across government; improving risk management approaches to reduce vulnerabilities in our current processes, including reduction of the total number of clearance holders and the backlog of periodic reinvestigations; and improving enterprise operations, to include strengthening oversight and government-wide implementation efforts while effectively managing limited resources.
More importantly, the review substantiated that “the current reinvestigation practices do not adequately reevaluate or appropriately mitigate risk within the security and suitability population. Lengthy periods between reinvestigations do not provide sufficient means to discover derogatory information that develops following the initial adjudication.” The risks associated with the infrequency of PRs, to evaluate character and conduct, and continued access were highlighted in the staff report by the House Committee on Oversight and Government Reform on Aaron Alexis.
From my perspective, there was little doubt that once CE was implemented, results would identify previously unknown/unreported issues. Multiple government agency pilots have consistently demonstrated the immediate need for CE implementation. For example, a DoD pilot tested the value and effectiveness of CE. The DoD pilot sampled 3,370 Army service members, civilian employees, and contractor personnel, and identified that 21.7 percent of the tested population had previously unreported derogatory information that had developed since the last investigation. In fact, three percent resulted in a revocation or suspension of a security clearance. If the Army sample is even marginally reflective of the rest of the cleared population, we have some very serious, yet to be identified, personnel security vulnerabilities out there right now.
So why, despite White House direction, Congressional mandates, Government Accounting Office (GAO) reporting, Security and Suitability reform priorities, and most importantly, the continued national security risks associated with the growing PR backlog and expanding reinvestigation periods…has CE not been implemented across the entire Executive Branch?
What’s Delaying CE Implementation?
Some might think that CE delays were caused by lengthy policy discussions taking place to ensure the right balance between personal privacy and the government’s need for information to address national security. However, in the case of CE, and the interpretation that CE was a continuation of background investigative activity, the policy hurdles were cleared pretty quickly.
Regrettably, the implementation delays for CE has been driven by the ongoing debate across the national security community on the developing guidance and oversight, and how to address the different technical approaches to CE. Instead of centralizing the process, multiple agencies are developing their own automated record check (ARC) and CE activities. In fact, the ODNI has allowed for “county options”, meaning agencies can choose to use one of four options to implement CE: 1) the ODNI ARC, 2) partner with an investigative service provider (ISP), 3) use the agency’s own ARC system, 4) or use a combination of ODNI, agency and ISP systems.
Unfortunately, the decision not to execute a standardized and centralized approach for CE will continue to result in implementation delays and will have long-term “downstream” consequences. First and foremost, cost. Decentralization leads to duplication and cost redundancies across the federal government. I understand many agencies want to incorporate CE results into their agency insider threat and risk management programs, however, that can certainly be done by receiving CE results from a centralized government ARC.
Second, and just as important, under a decentralized approach, what happens to information collected through CE and the federal government’s responsibility to meet statutory guidelines for reciprocity? Title III of Intelligence Reform and Terrorism Prevention Act (IRTPA) established statutory guidelines for reciprocity of security clearances. This act provided congressional direction that all legitimate government clearances are to be accepted and transferable between and among government agencies. Current cross government CE strategies fail to appropriately document and share results. So, what happens if CE information fails to be reported and incorporated into the subject’s investigative record?
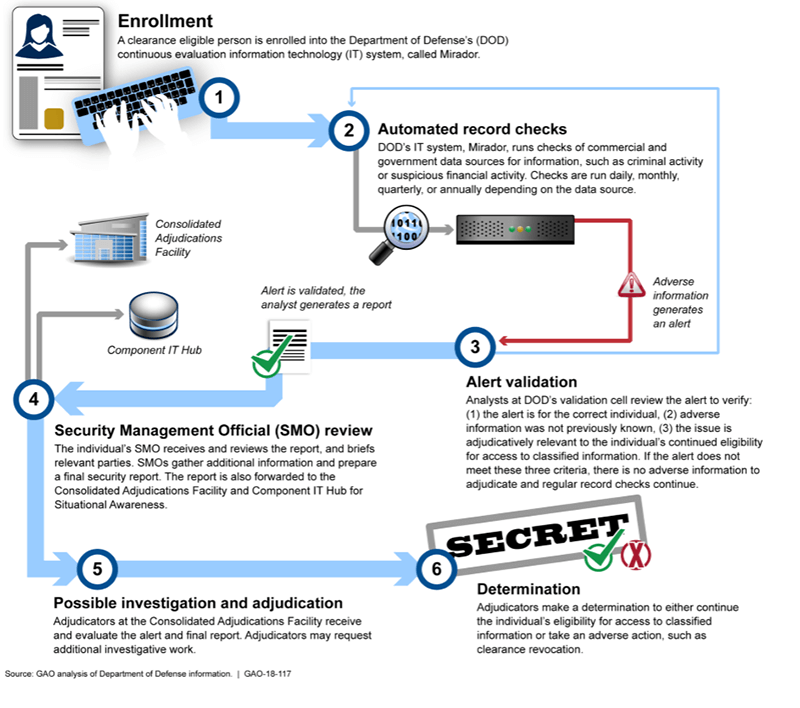
Case in point, the recent GAO report on CE illustrated the Department of Defense CE evaluation process.
What is missing from the process is the documentation of CE results in the subject’s security or background investigative file. Today, the Central Verification System (CVS) contains information on background investigations, credentialing determinations, suitability determinations, security clearances, Personal Identification Verification (PIV) credentials, polygraph data and is used as the primary repository for making reciprocity determinations. The failure to document and report the CE results will result in incomplete information being available for a “reciprocity” review.
Years of security clearance reform efforts to align investigative and adjudicative standards across the government to save money, reduce redundant investigative activity, and ensure reciprocity will be lost. In addition, when periodic reinvestigations are conducted, the automated record checks used for CE, will have to be accomplished again, because the results were not made available to the ISP. In fact, CE information that may have already been collected and adjudicated by the agency (but not shared), would subsequently be collected again during the PR and presented to the agency as new information, wasting the time of both the ISP and agency adjudicators.
That doesn’t mean CE is doomed. In a follow-up, we consider how to ensure the CE program succeeds.